Lock Down Your WordPress Installation
Very few things in the world are more annoying – or can be more devastating to a business – than having your server or your WordPress hacked. Someone goes to visit your site and either sees a blacklisted warning from search engine providers…and being blacklisted by search engines is a virtual death sentence for your business online. Every dime you’ve spent on building your website, building an email list, developing a presence in search engines – it’s all down the drain. Once your domain is blacklisted, it’s basically over.
If your WordPress site has been hacked, you’ll find a great article on how to fix it here. Of course, you can call us! We fix that.
So, what do you do to protect your investment? Here are a few simple tips that can make your WordPress installation more secure and protect your online reputation and the data security of your customers and your clients.
-
Don’t have a user named “admin” on your site. At all.
Most hackers are well aware that the default username for WordPress is “admin”. Since a username and password are required to log into WordPress, why give hackers 50% of what they need to walk through the door? It’s like giving someone the key to your deadbolt and just making them pick the standard lock on your house to get all the way in. Why take the chance? Here’s how you fix it.
a. Log in to your WordPress Admin Panel, hover over users and select “Add New”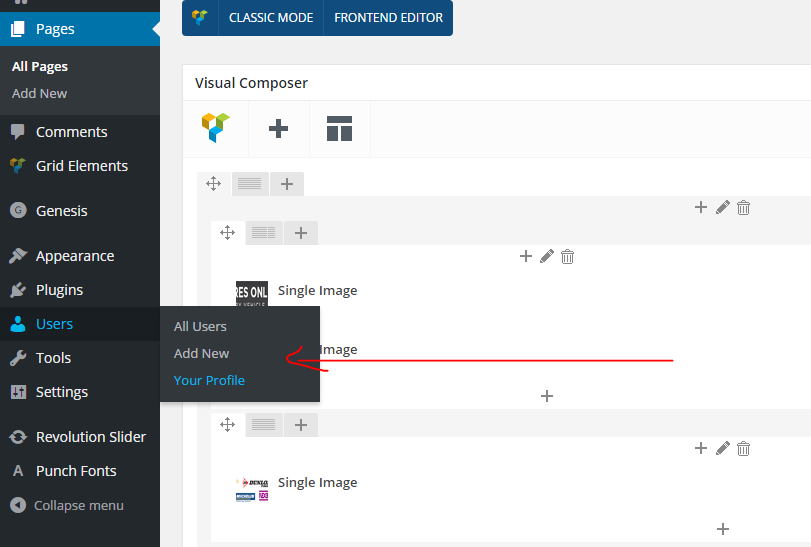
b. Fill in the required information and provide administrator permissions for that new user.
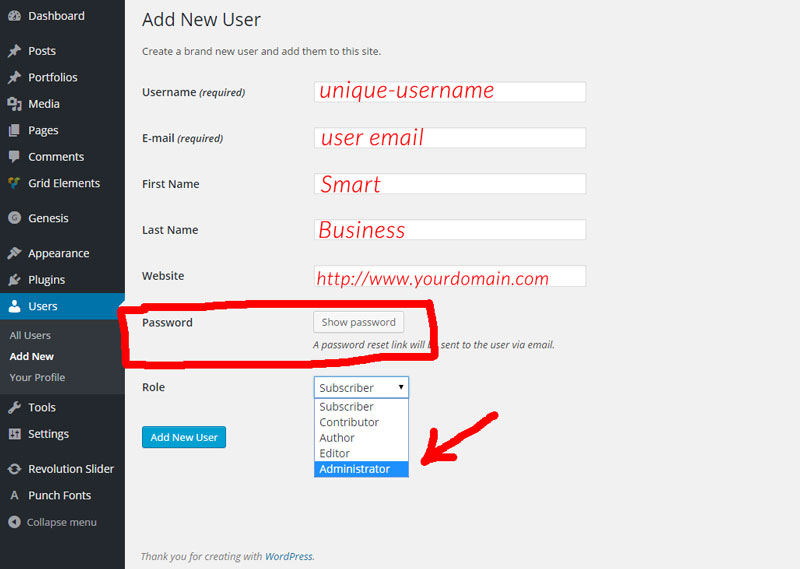
c. Log in with the new identity
d. Delete “ADMIN” and remove that particular security risk from your WordPress installation -
Make sure to change your authentication (SALTS) in your wp-config.php file
There’s a big, long, drawn-out explanation of how WordPress keys work…and I’m not going to go into it. The nutshell version is these keys work with data encryption and make your site more secure. You can read more about it on the WP Beginners Blog. Out of the box, though, these keys are not defined in wp-config.php — they are the same on EVERY WordPress installation, and any hacker can find these keys fairly easily if they aren’t changed. Data collection doesn’t get much easier than that. So, here’s how to fix it (it’s not nearly as terrifying as it sounds, even if you’ve never opened a PHP file in your life).
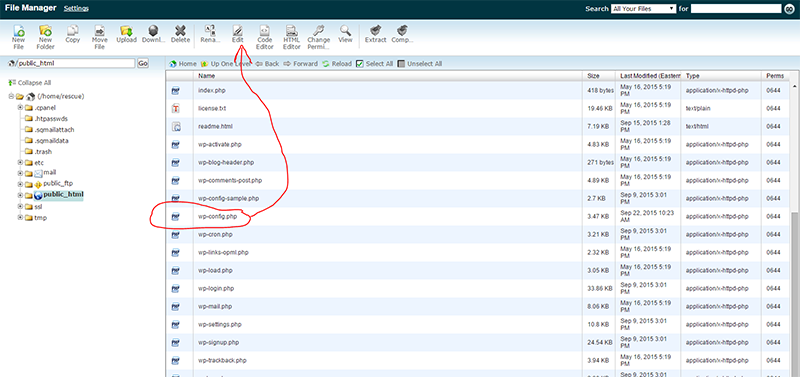
a. Log into your hosting account or FTP into your server root directory (hahaha – sounds just awful, doesn’t it?!). This is NOT logging into yourdomain.com/wp-admin – this is done at the server level. So, get logged in and look for the file named wp-config.php.
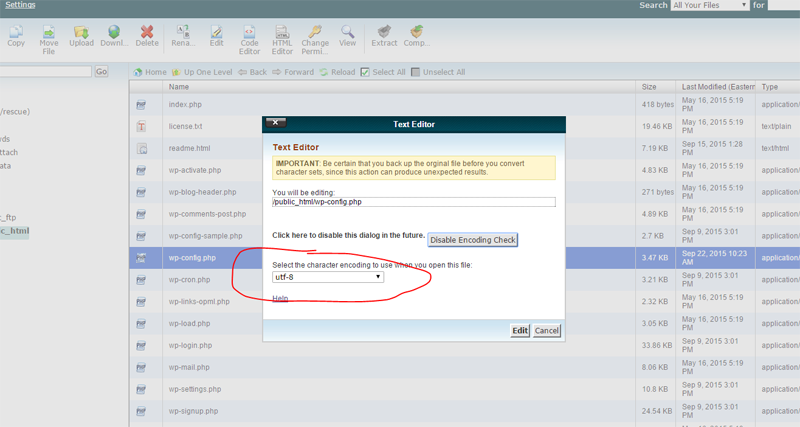
b. Open the file in EDIT mode. You’ll see a warning about encoding. It is generally set to UTF-8, so just click EDIT in the lower right.
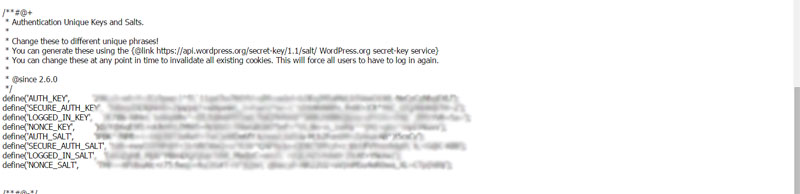
c. With the file open, look for this text: “Authentication Unique Keys and Salts.” What you’re specifically looking for is the code beneath that looks like this:
define(‘AUTH_KEY’, ‘put your unique phrase here’);
define(‘SECURE_AUTH_KEY’, ‘put your unique phrase here’);
define(‘LOGGED_IN_KEY’, ‘put your unique phrase here’);
define(‘NONCE_KEY’, ‘put your unique phrase here’);
Now, open this URL for the WordPress Key Generator tool to get new keys.
d. Copy the information from the key generator and paste it over the code that matches in your wp-config.php file. Click save and then close the document. All done and you’re safer already! -
Change the database table prefix – EVERYONE knows that wp_ is the default.
One of the things that makes WordPress so awesome is also one of the things that makes it vulnerable for users who aren’t really “nerds.” Those cool WordPress defaults that make it so, so easy to install and set up can be a real threat to the security of your installation if you aren’t aware of the risks. So….here’s how you change the table prefix in WordPress (helpful hint – do this while you’re still logged into your server and in the right directory. I’m TOTALLY joking! There is a manual way to do this, and I do it for all of my clients, but you can simply install the WP SECURITY plugin and follow the prompts to make your WordPress installation more secure. BACK UP YOUR DATABASE FIRST!
-
Put some ROBOTS to work for you!
Seriously – the robots.txt file does NOT come as a default feature in WordPress and it’s easy to configure this file to prevent search engine spiders from accessing your admin area. While you’re in your root directory (same place you went to configure your wp-config.php file), simply follow the instructions in this brief video. For convenience, here’s the code to paste into the new file you’re going to create.
#
User-agent: *
Disallow: /cgi-bin
Disallow: /wp-admin
Disallow: /wp-includes
Disallow: /wp-content/plugins/
Disallow: /wp-content/cache/
Disallow: /wp-content/themes/
Disallow: */trackback/
Disallow: */feed/
Disallow: /*/feed/rss/$
Disallow: /category/*
For those of you who don’t have any interest in doing this but still want to protect your investment in your website, feel free to CONTACT ME for help!
